Configure Azure Files Permissions for MSIX App Attach
Nerdio Manager leverages Azure Files share technology to store MSIX App Attach packages and associated metadata. You can use an existing Azure Files share or create a new one with Nerdio Manager.
Note: The Azure Files share must be AD-integrated to be used as an App Attach storage location in Nerdio Manager.
Once you've created an Azure Files share and joined it to your AD domain, you must configure security settings on the share to allow session hosts and users to read the contents of the App Attach packages. With Azure Files, the security settings are configured in the following places:
Azure Files Access

NTFS Permissions
In these places, both the session host VM computer and user who uses the application must have at least Reader access. By default, the NTFS permissions on newly created Azure Files shares already have the necessary configuration. However, Azure Files share Access Control still needs to be configured.
To grant session host VMs access to Azure Files shares:
-
In Active Directory, create a new Global Security group in an OU that is being synched to Entra ID with ADConnect.
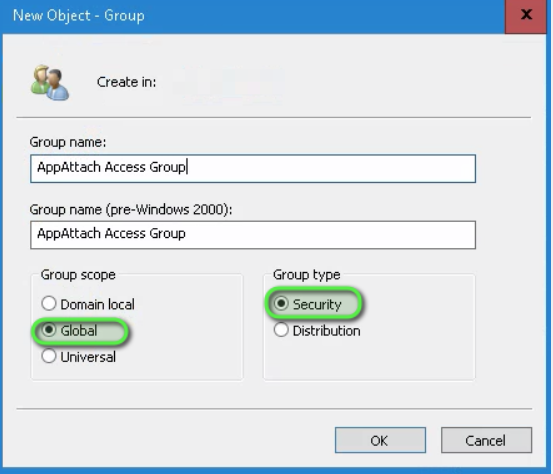
-
Add Domain Computers and Domain Users to the new group.

-
In Azure portal, find your Azure Files share and navigate to Access Control.
-
Add the new security group with Storage File Data SMB Share Reader role.
Note: You may need to wait for the next sync cycle for new groups to be available in Entra ID.

Note: The end result is read-only access to the Azure Files share by all domain users and computers. Feel free to customize the above procedure to suite your organization's security policies.